Blogpost - Infrastructure as Code (IaC)
Infrastructure as Code (IaC) and Terrascan: A Guide
In today’s fast-paced IT world, companies are constantly looking for ways to manage their infrastructure more efficiently and securely. Infrastructure as Code (IaC) has emerged as a revolutionary approach that enables defining and managing infrastructure resources through code. In this blog post, we will discuss the benefits and challenges of IaC and show how Terrascan can help improve the security of your IaC implementations.
By automating infrastructure through code, security policies and compliance standards can be directly integrated into configuration files. This ensures that all deployed environments are configured consistently and according to the established security standards. Manual configuration errors that could lead to security vulnerabilities are minimized. IaC also enables faster detection and resolution of security risks. Since the entire infrastructure is represented in code, security checks and code scans can be automated. Tools like Terrascan or AWS Config can be used to check IaC code for known vulnerabilities or compliance violations before changes are applied to the production environment.
Additionally, IaC facilitates patch management and the updating of security policies across all systems. Changes need only be made in the code and can then be automatically applied to all relevant resources.
Overall, IaC helps strengthen a company’s security posture by providing consistent, auditable, and automated processes for infrastructure management.
What is Infrastructure as Code (IaC)?
Infrastructure as Code is an approach in which IT infrastructure such as networks, servers, and services are defined and managed through declarative code. Instead of manually configuring hardware or setting up servers, developers and system administrators can write scripts to automate these tasks. This leads to more consistent, efficient, and scalable infrastructure management.
Popular IaC Tools
- Terraform: An open-source tool by HashiCorp that provides a unified syntax for defining infrastructure across various cloud providers.
- CloudFormation: A service by AWS that allows defining AWS resources using JSON or YAML templates.
- Ansible: An automation tool for configuration management, application deployment, and orchestration.
Benefits of IaC
Automation and Efficiency
By automating infrastructure processes, companies can save time and reduce human errors. Scripts can be executed multiple times to create identical environments, which is particularly useful in test and production environments.
Consistency and Repeatability
IaC ensures that environments remain consistent. Since the infrastructure is defined as code, teams can ensure that each deployment uses the same parameters and configurations.
Versioning and Collaboration
As IaC files can be stored in version control systems like Git, it’s easier to track changes, restore older versions, and collaborate in teams.
Challenges of IaC
Complexity
Managing large IaC codebases can become complex. Teams must ensure that the code is well-organized and documented to maintain its manageability.
Security Risks
Misconfigurations in the code can lead to security vulnerabilities. Without proper security checks, sensitive data could be exposed, or unauthorized access could be allowed.
Introduction to Terrascan
Terrascan is an open-source tool developed to perform security and compliance scans for IaC configurations. It analyzes code to identify potential vulnerabilities before the infrastructure is deployed.
Infrastructure as Code: Principles, Patterns, and Practices:
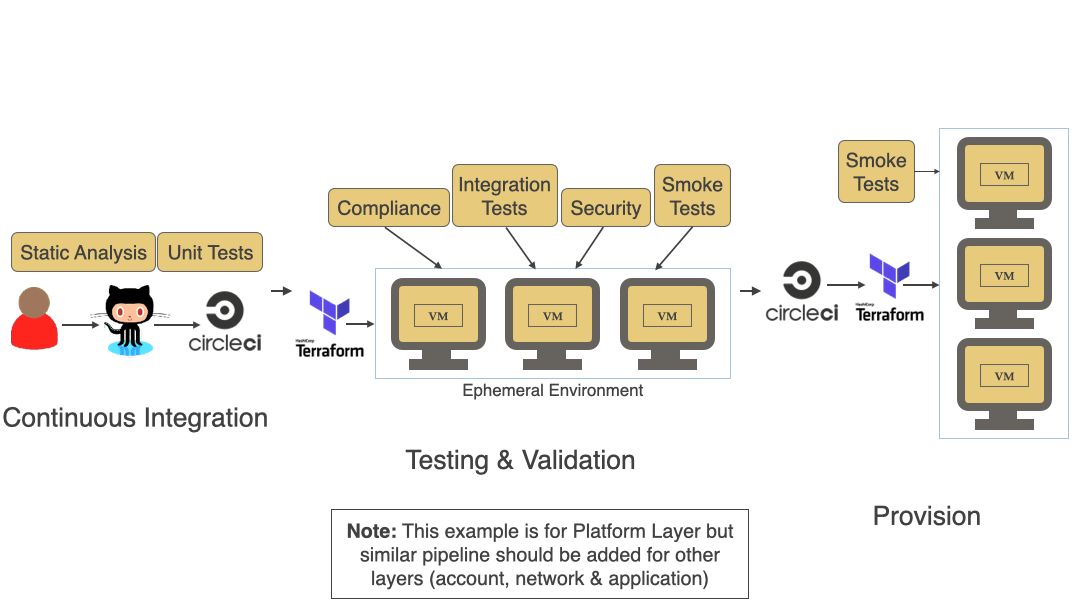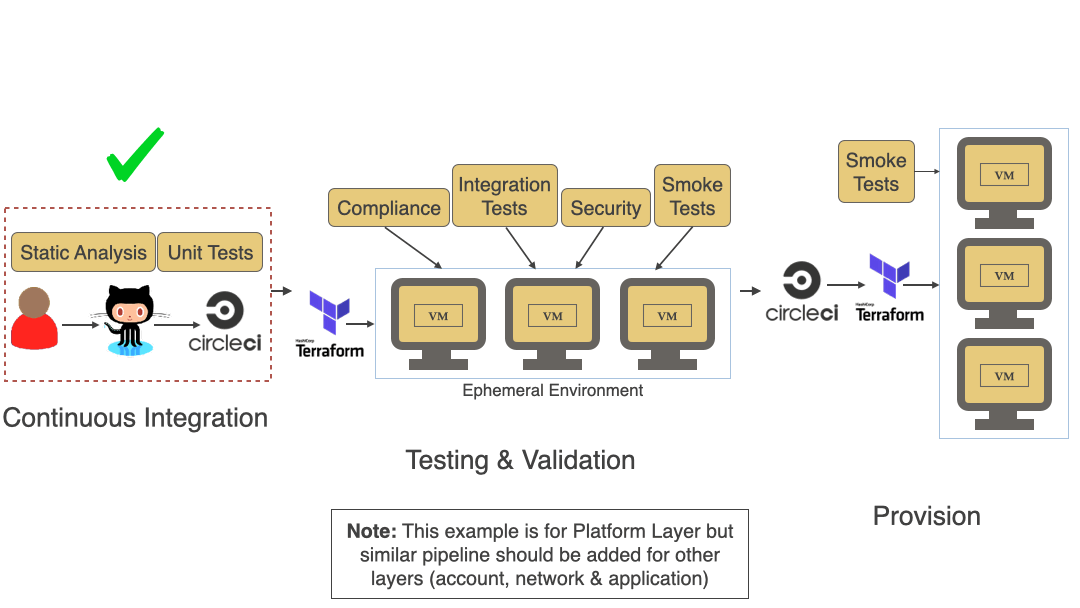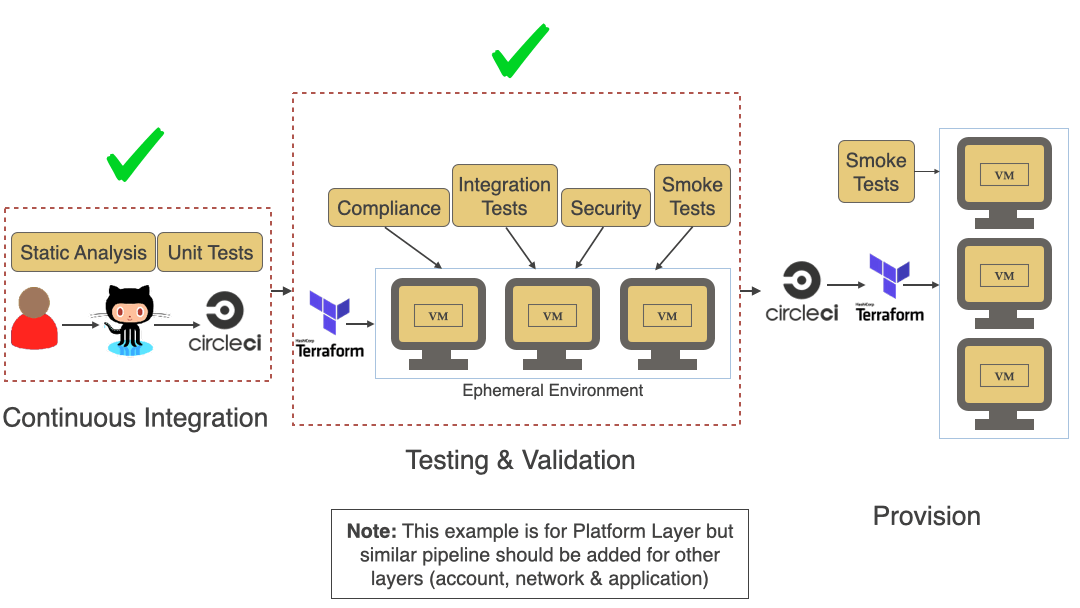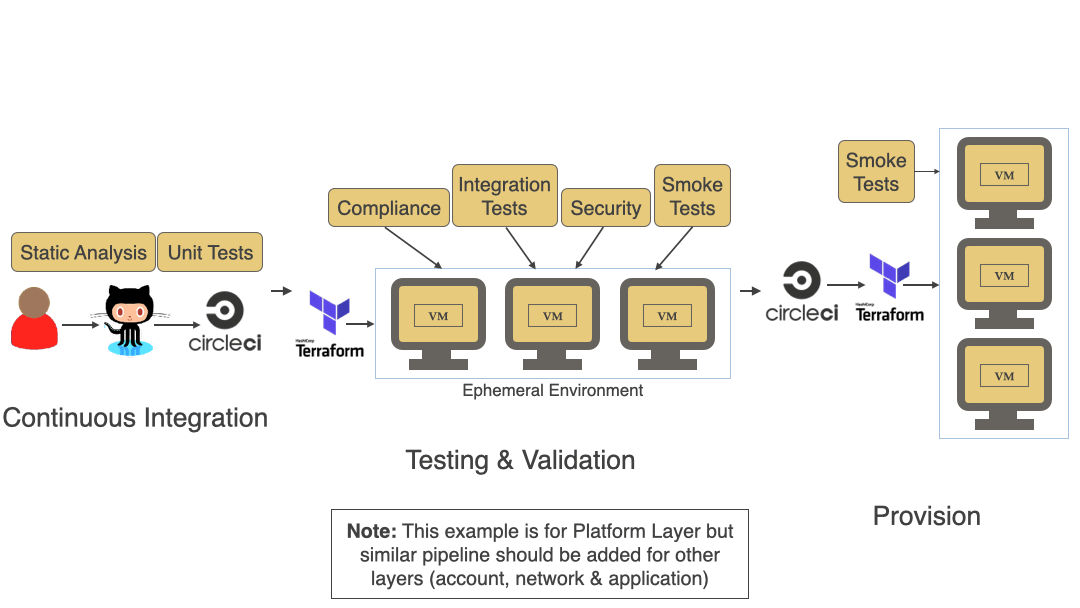
Terrascan supports a modular architecture that enables the integration of various IaC platforms and formats:
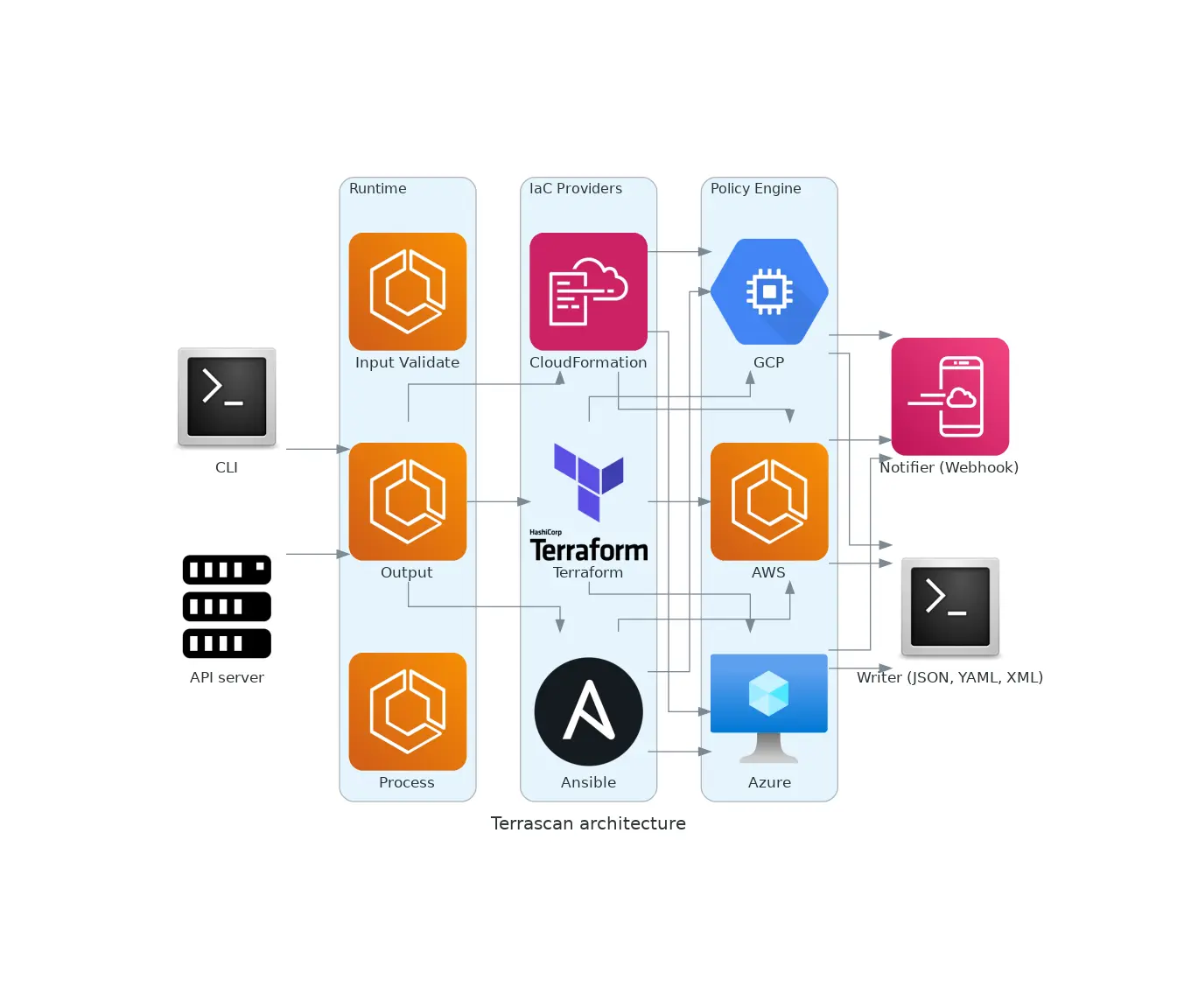
Terrascan Features
- Security Scanning: Detects insecure configurations such as publicly accessible S3 buckets or missing encryption.
- Compliance Checks: Validates code against compliance standards like CIS, PCI-DSS, and HIPAA.
- Integration: Can be integrated into CI/CD pipelines to perform automated scans.
Code Examples for Terrascan
1. Installing Terrascan
# Installation via Homebrew (for macOS)
brew install terrascan
# Installation via Binary Release (for Linux)
wget https://github.com/accurics/terrascan/releases/latest/download/terrascan-linux-amd64
chmod +x terrascan-linux-amd64
sudo mv terrascan-linux-amd64 /usr/local/bin/terrascan
2. Scanning a Terraform Configuration
Assuming you have a Terraform file main.tf that defines your infrastructure:
# Running the scan
terrascan scan -t terraform -f /path/to/main.tf
Terrascan analyzes the file and provides a report of identified security issues.
3. Example of an Insecure Terraform Configuration
resource "aws_s3_bucket" "b" {
bucket = "my-website-bucket"
acl = "public-read"
}
In this example, the S3 bucket is publicly readable, which poses a security risk. Terrascan would detect this and issue a warning.
4. Integration into a CI/CD Pipeline (e.g., GitHub Actions)
name: CRYPTRON Terrascan Security Scan
on:
push:
branches: [ "main" ]
jobs:
terrascan:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Run Terrascan
uses: accurics/terrascan-action@v1
with:
iac_type: "terraform"
directory: "."
This workflow runs Terrascan every time changes are pushed to the main branch, ensuring that security issues are detected early.
Terrascan outputs its results in a human-readable format by default.
By default, Terrascan outputs its results in a human-friendly format. Table Output Details Terrascan Violation
|
Best Practices with Terrascan
- Regular Scans: Run Terrascan regularly to identify new security risks.
- Custom Rule Sets: Adapt the default rules to fit your organization’s requirements.
- Training: Educate your team on the importance of security in IaC.
Conclusion
Infrastructure as Code (IaC) is revolutionizing how we manage and deploy IT infrastructure. Instead of manually configuring hardware and software, IaC allows defining infrastructure components through code, leading to greater efficiency, consistency, and scalability in infrastructure management.
While IaC offers numerous benefits, the associated security aspects must not be neglected. Misconfigurations or security gaps in the code can have serious consequences and endanger the entire IT infrastructure of a company. Without appropriate security measures, automated processes can inadvertently introduce vulnerabilities.
This is where tools like Terrascan come into play. Terrascan is an open-source tool specifically designed to check IaC configurations for security and compliance violations. It analyzes the infrastructure code and identifies potential vulnerabilities before they reach the production environment. This allows issues to be addressed before they cause damage.
By integrating Terrascan into your development processes, you can ensure that the infrastructures you define are not only functional but also secure and compliant with applicable standards. Automated security checks become an integral part of the development cycle, increasing the quality and security of the deployed resources.
Early identification and remediation of security risks enable you to minimize potential threats and ensure a more robust infrastructure. This fosters a culture of "Security by Design," where security aspects are integrated into development processes from the beginning. Overall, this helps strengthen trust in your systems, meet compliance requirements, and optimize operational processes.
The CRYPTRON Security Team is happy to advise you on Infrastructure as Code (IaC). If you have any questions about Infrastructure as Code (IaC), please feel free to contact us.
References / Links:
- Terraform by HashiCorp
- GitHub - tenable/terrascan: Detect compliance and security violations across Infrastructure as Code
- Infrastructure as Code Security - OWASP Cheat Sheet Series
- What is infrastructure as code (IaC)? - Azure DevOps | Microsoft Learn
- Top 7 IaC Pitfalls - Risks, Challenges, Solutions (daily.dev)